Cyber Threats are Real: Protect Yourself with Acronis
Protect your company with Kerr's Acronis Security Platform
- Email Security starting as low as $3.99 per email box
- Automated Backups of your Critical Servers
- Data Loss Prevention and Disaster Recovery
- Active, "always on" protection for all your devices
Stay ahead of today’s advanced email attacks
Email is the #1 threat vector for cyberattacks
All businesses face the same daunting challenge: email is the most important business communication tool and the leading attack vector for security breaches.
Protect your business’s email from modern threats
Cybercriminals weaponize email in many ways — whether it’s to introduce malware into an organization’s systems, steal data, or use social engineering for financial gains. You need capabilities that can quickly detect and block advanced threats from incoming email, so you are able to protect your company’s brand, reputation and data
What is Email Security Managed Service?
Our services help you plan, implement and secure your organization with the most effective next-generation technologies and expertise. Email Security Managed Service provides the most comprehensive protection against the multitude of email threats.
90% of attacks originate with an email
$4.24 Million: Global average cost of a data breach in 2021
58% surveyed lost 3 hours or more as result of spam
Target and Prevent Threats with our solution
Did You Know?
Phishing is a type of online scam where an attacker impersonates a legitimate organization via email,
text message or advertisements to trick a victim into revealing sensitive information to the attacker, or to
deploy malicious software on the victim’s device.

Our Acronis platform offers proven regulatory compliance:
What People Say About Us
Learn More
Add On Advanced Disaster Recovery With CyberProtect Cloud
When was the last time you lost power and/or the internet crashed? What was the impact to your business? Did you lose any data or revenue? The truth is that everyday system outages and cyberattacks are shockingly common. When something bad like this happens, it’s not only frustrating, it can be devastating to your bottom line. That’s why it’s important to prepare for any IT disruption.
Disaster Recovery for All Your Servers
Minimize downtime by enabling easy, scalable and efficient cloud-based recovery of servers
"Point in Time" Recovery to the Minute
Restore systems and data to any recoverable point in the past, instead of to the latest one.
Malware Free Recovery
Eliminate the possibility of reinfection by checking the list of recovery points available for failovers to see if a malware or other indicator of compromise is discovered during the
backup scanning process.
Failover Protection: Recover Quickly
Ensure quick and easy automated failover of the client’s production environment to an offsite server running in Acronis Disaster Recovery Storage or to a hot storage location in the Acronis Cloud.
IPsec Multisite VPN Support
Strengthen security with IPSec multisite VPN support that integrates secure protocols and algorithms, so you can easily support clients with multiple sites that are hosting critical data.
Stay Compliant
Gain visibility into disaster recovery orchestration with a detailed runbook-execution real-time view and execution history.
Disaster can strike a business at any moment
Your business is at risk every day. Your company needs to keep operations up and running; no matter what; but some things are beyond your control. Storage fails, files get lost, power blacks out, and datacenters go offline. It happens, but random accidents shouldn’t impact your business. Simple daily backups are no longer enough to ensure your business can keep systems up and running in the event of disaster. If disaster does strike, how can you ensure that your business and its technology have the resilience to protect data and are able to recover quickly?

Disaster Recovery Managed Services explained:
What are Disaster Recovery Managed Services?
Our services help you plan, implement and secure your business with the most effective, next generation technologies and expertise. Disaster recovery Managed Services enable outstanding business continuity and complete protection of your data with backup and disaster recovery in a single solution for your business. We design an environment prepared for the unexpected. We will establish, execute and support your business continuity strategy by ensuring your business is up and running even in the event of an unplanned outage. If the worst happens, we can quickly spin up your IT systems in the cloud allowing you remain operational and avoid costly downtime and data loss. With Disaster Recovery Managed Services you get complete peace of mind knowing you are safeguarding your data, employee productivity, and business.
RPO and RTO: Understanding the differences
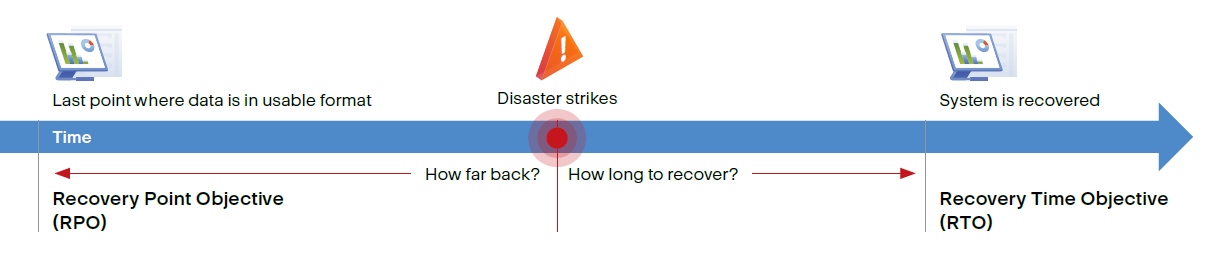
Recovery Point Objective (RPO) and Recovery Time Objective (RTO) are two of the most important aspects of your disaster recovery plan: RPOs refer to the amount of data that can be lost before significant harm to your business occurs. RTO refers to how much time an application can be down without causing significant damage to your business.
What steps will our team take implementing your business’s Disaster Recovery Managed Services?
- Take inventory and define your business’s key assets: We help prioritize your assets; whether business critical, important or noncritical. By doing so, it will help focus on recovering the most vital assets first so that your business can begin functioning again as quickly as possible.
- Help you decide the best recovery window: What period of downtime can your business sustain? Is it within minutes, hours, days? This is done when defining your RTO and RPO.
- Define your recovery solution: We will help determine the best way to replicate your data between multiple disaster recovery sites.
- Test the disaster recovery solution and thereafter manage and maintain it: Even backups can fail in a disaster, so its paramount to test your replicated data and ensure it can be restored back to your business’s site. We repeat this step periodically to ensure the setup is working.
Calculate the Cost of Downtime
The fact of the matter is that no business is immune from downtime, whether at the hands of Mother Nature,
employee error, or even a cybercriminal. These factors can be applied to calculate actual downtime cost per
hour. Bottom line? Downtime risks losing big money for your business.










